• CCP Directive: Data is now a production input, equal to labor, capital, land, and technology.
• Data: Any record of information in electronic or non-electronic form (Art. 3).
• Data Security: The ability to ensure data under effective protection and in lawful use, and remain so through taking necessary measures (Art. 3).
• Data Processing: Includes activities such as the collection, storage, use, refinery, transfer, provision, or public disclosure (Art. 3).
• The DSL aims to classify and protect data based on its relevance to the state's economic development, national security, public interest, and individuals' and entities' legitimate rights and interests.
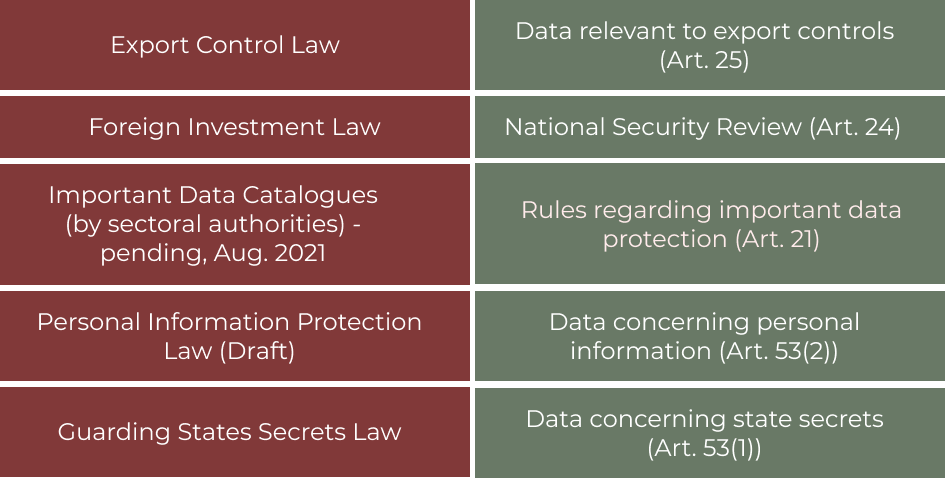
• Using the class-based system as a guide, the DSL requires relevant parties to coordinate with related authorities to provide a list of important data to strengthen the protection of the relevant data.
• The DSL further introduces the concept of core state data and emphasizes that the state will implement a strengthened management system in relation to the core state data.
• The DSL also empowers regional and industry authorities to formulate catalogs of relevant data and measures to protect such data in their respective areas.
• The highest level of the three-level system.
• Refers to data that “have a bearing on national security, the lifelines of national economy, people’s key livelihood and major public interests." (Art. 21)
• The national core data are subject to a stricter management system by the state than important data.
• Middle level of the three-level system.
• Undefined by the DSL. However, the DSL provides that (1) the national data security work coordination mechanism shall coordinate with the relevant parties to formulate the catalogues and (2) each region and department, in accordance with the three-level classification data system, will determine the list and undertake the protection of the important data for their respective industries and sectors. (Art. 21)
• Meanwhile, other cybersecurity and information security legislation define important data as related to "national security, economic development and public interests, but do not involve the national secrets".
• Under the DSL, the listed responsibilities under the three-level data classification system are vague and broad. As of August 2021, their precise terms and obligations are yet to be clarified.
• In February 2020, the issuance of the Classification Guidance for Industrial Data (for Trial Implementation) by the Ministry of Industry and Information Technology shows classification of industrial data has taken place.
• It is likely more data protection classification guidance or similar standards will be issued.
• The DSL requires that a unified, effective, and authoritative system is established to evaluate, report, share, and monitor data security risks but does not elaborate on the details, which are pending future regulations and/or national standards.
• Mechanism for data security risk assessment, reporting, information sharing, supervision, and early warning (Art. 22)
• Response mechanism to data security emergency (Art. 23)
• National security review mechanism (Art. 24)
• Export control mechanism (Art. 25)
• Anti-discrimination mechanism (Art. 26)
• Refers to important industries and fields that may seriously endanger national security, national economy and people’s livelihood, and public interests.
• State Council: guides and supervises the safety protection of critical information infrastructure
• Other Relevant Departments: security protection and supervision and management of critical information infrastructure.
• Operators: adopt technical protection measures and other necessary measures to respond to cybersecurity incidents and prevent cyberattacks in accordance with these regulations.
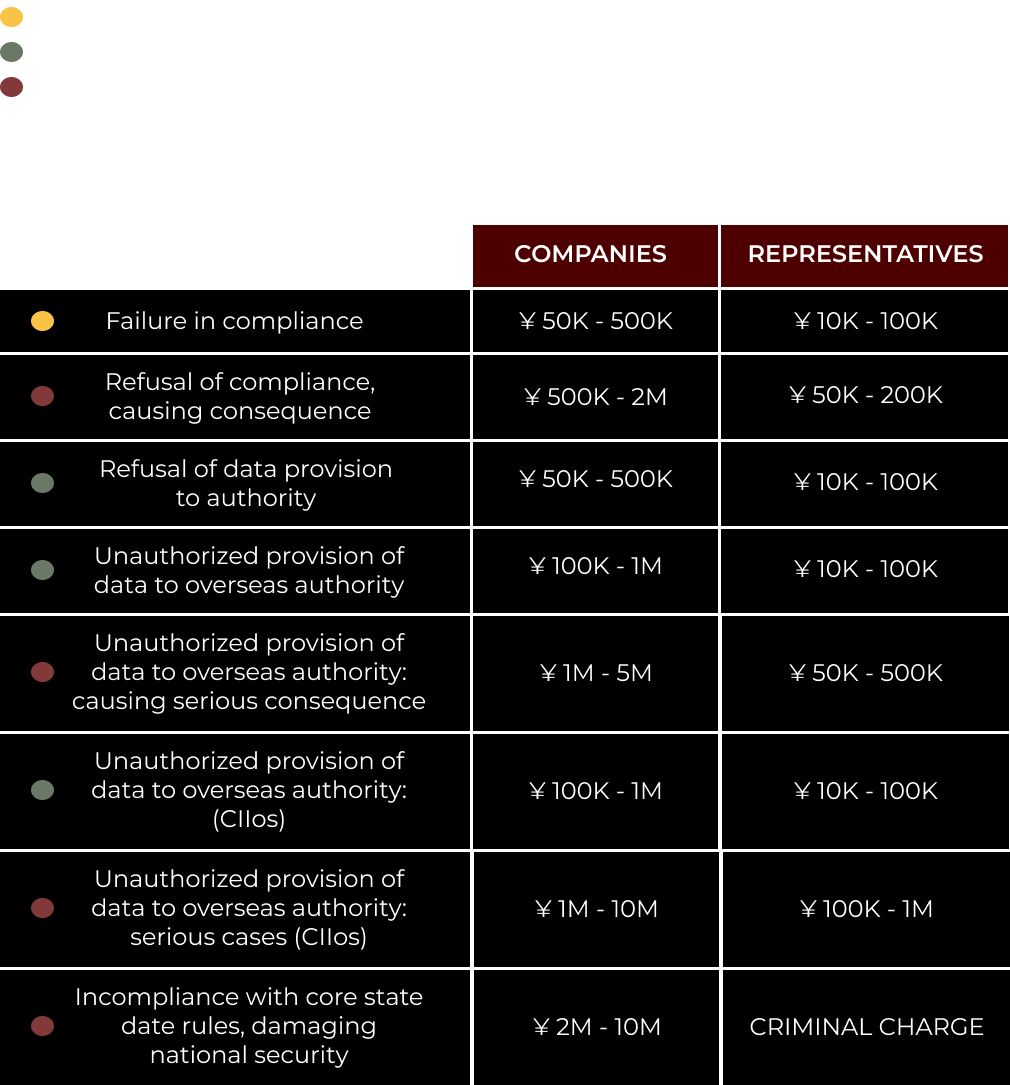
• Penalties: Non-compliance of operators shall result in an imposition of a fine of 100,000 yuan up to 1 million yuan.
• Effectivity: 1 September 2021
• On 17 August 2021, the State Administration for Market Regulation (SAMR) issued a set of draft regulations banning unfair competition and restricting the use of user data.
• In the draft, SAMR stated the following:
• Business operators should not use data or algorithms to hijack traffic or influence users' choices. They may also not use technical means to illegally capture or use other business operators’ data.
• Companies would also be barred from fabricating or spreading misleading information to damage the reputation of competitors and need to stop marketing practices like fake reviews and coupons or cash incentives used to entice positive ratings.
• The State Council said any purchases of internet products and services that may affect national security by operators should go through security scrutiny.
• Risk monitoring, remedy, and incidents reporting
• Conduct training and education
• Collaborate with domestic law enforcement effort
• Follow the purposes and scope of data collection as stipulated by authorities
• Security management system
• Adopt needed technologies and other measures
• Report to authority and let them handle overseas request for domestically collected data
• Carry out MLPS (2.0) & follow-up with classification and hierarchical protection
• Management organ with designated personnel
• Regular risk assessment and reporting
• Follow specific rules for data importing
• Wait for catalogues for important data
• Follow Cybersecurity Law when exporting data
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-performance | 1 Day | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 1 Day | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-others | 1 Day | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-functional | 1 Day | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 1 Day | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| viewed_cookie_policy | 1 Day | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |